Intrusion detection and defense system
Intrusion detection and defense system
Introduction

ABT intrusion detection and defense system of IPS-7000 series is an industry-leading IPS product developed by Beijing ABT Technology Co., Ltd. Deployed on the key nodes of the network in an online or bypass way, it can conduct 2- to 7-layer full inspection and analysis on the data, provide powerful Web protection functions, block and record in real time viruses, worms, Trojans, spyware, web tampering, injection attacks, cross-site attacks, DDoS attacks, vulnerability scanning, anomaly protocol, phishing and other network attacks in the network traffic, and effectively manage IM software, P2P tools, streaming media, online games, stock software and other network abuse behaviors. Additionally, it also integrates effective bandwidth management, URL filtering and keyword filtering functions, and provides the most comprehensive, perfect IPS solutions in the industry. ABT IPS provides different grades and models of products for multipleservice application scenarios including data centers, large-scale network boundaries andSMEs.
Features
Original security attack and defense exercise laboratory
ABT has set up the original security attack and defense exercise laboratory in the industry. In the laboratory, the latest attack tester and other professional equipment are equipped to simulate a variety of attacks on the Internet, truly realizing "be prepared for danger in times of safety". All feature libraries released by the security team must go through practical exercise in the internal attack and defense laboratory before being provided to users, so as to ensure with the rigorous process that the services are delivered to customers timely and the customers are assured.
Fine, timely intrusion detection feature library
After years of precipitation and accumulation in the field of network security, ABT has created a senior attack feature library team and security service team. They concern the industry's newly discovered security vulnerabilities and receive the attack features fed back from global users at any time, respond and provide updates in the first time, perfect attack feature library in real time and provide the most timely and most comprehensive intrusion defense.
Keeping away from malicious mails
ABT intrusion detection and defense system has a strong anti-spam function. In addition to the authentication of sources such as the recipient and the sender, it can realize anti-spam mail features through the limitation on SMTP connections, limitation on e-mail size and keyword filtering in the e-mail contents, and flexibly self-define the spam mailpolicy according to the service situation. In addition, the anti-spam mail policy can also filter spam mails based on the "Bayesian" algorithm, making policy deployment easier and smarter.
Flexible networking mode
ABT intrusion detection and defense system supports network features such as MCE, IPSEC, 802.1Q, GRE and VRRP, supports online or IDS bypass mode deployment, and supports routing mode, transparent mode and mixed mode, realizing flexible networking in any complex network environment.
Convenient management method
ABT intrusion detection and defense system supports local management and centralized management. In case of a single-unit or small-scale deployment, the local command line or built-in WEB interface can be used for graphical management; in case of large-scale deployment, the unified configuration policy issue, attack event monitoring and attack event analysis can be realizedfor the distributed IPS intrusion prevention system through ABT centralized management system.
High reliability
Supporting redundant power, software bypass and hardware bypass, ABT intrusion detection and defense system can ensure network reliability at all levels. It will not become network failure point while realizing comprehensive security protection,thus improving network reliability.
Deployment method
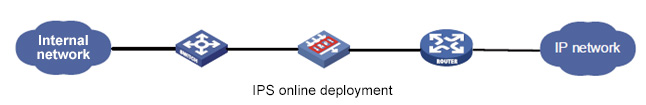
IPS online deployment method
Deployed in the key path of the network, it can achieve 2- to 7-layer real-time in-depth analysis on the data passed, defends internal and external attacks and manages two-way traffic.
IDS bypass deployment method
It monitors and analyzes network traffic, records attacks and makes alarm.