Cloud Security
Industry cloud classified security protection solution
Over the past 3 years, global cloud computing market scale has been growing by about 17% on average every year; scale growth rate of cloud security service market has been a little higher at about 23%, highlighting the importance of cloud security; according to authoritative statistics, in 2016, China’s private cloud market scale was as high as RMB34.48 billion, 25.1% higher than that in 2015. It is estimated that China’s private cloud market will be growing steadily in 2017-2020. By 2020, the market scale will be up to RMB76.24 billion, which is bound to push the sustained growth in domestic overall cloud security service market.
The main security threats of today’s cloud computing environment are data leakage, certificate stolen, API being hacked, system vulnerability taken advantage of, account hijacking, malicious insider, APT unknown risks, permanent data loss, cloud service abuse, denial of service attack and shared technology threats; Investigations show that 64% of enterprise choose private cloud out of security reasons. Compared with 2015, security is still the major factor for organizations to use private cloud. With the implementation of Network Security Law and the commencement of classified protection 2.0, the cloud security solution is sure to move toward the direction of rigid demand+ compliance.
Overall design idea of ABT cloud security solution
One security system: construct the next security defense system in the cloud environment with service security as the core and security platform as the pillar.
Three security lines: shape a center with three security lines and build a defense system in depth that are in accordance with the security construction standard mechanism on the basis of operation features in the cloud environment.
Four security capabilities: risk forecasting capability, attack-defense capability, threat detecting capability and event responding capability.
Security capability center: integrate third party’s security capability through the standard interface; drive security resources with unified security policies to make the security system software, automatic and flexible.
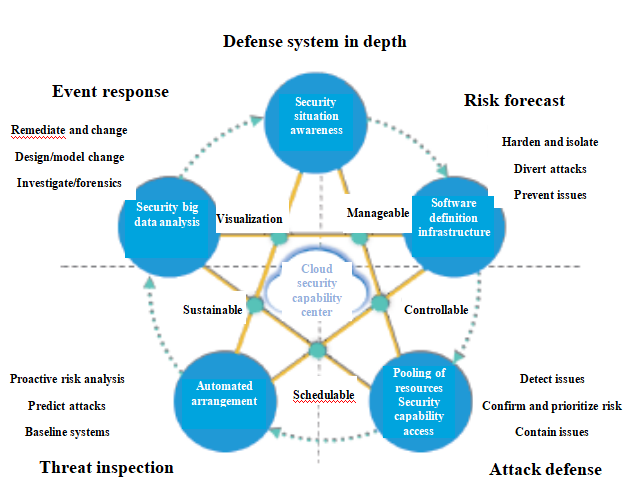
ABT security core controller design
Aiming at user demands, ABT organizes and arranges all network service units orderly to meet users’ security demands with balanced and coordinated services, realizing security capability access and automated arrangement in the cloud computing environment finally.
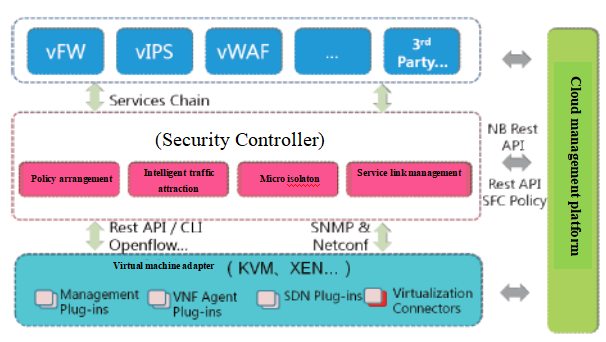
Construction of security defense system by pooling of actual resources and service chain
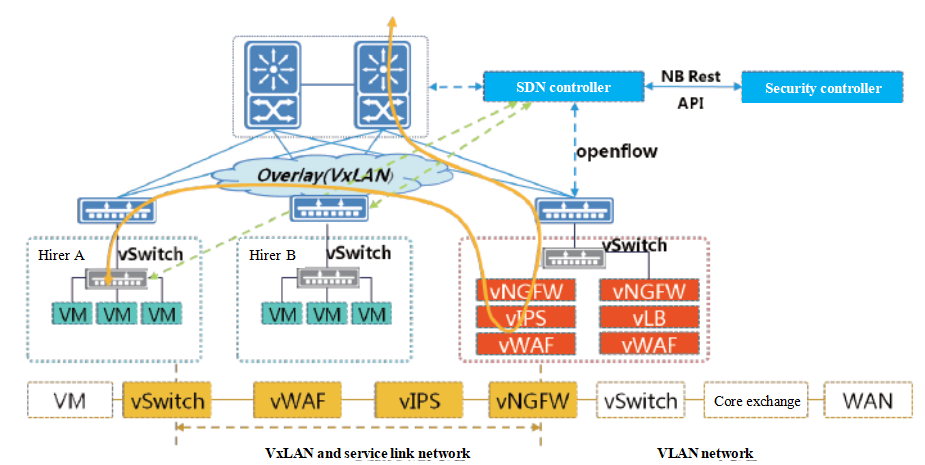
After receiving and analyzing security policies, the security control platform send traffic attraction policy with SDN controller;
VXLAN, vNGFW or vRouter corresponds to different hirers. They work as VXLAN IP Gateway that terminates hirers’ VXLAN traffic and convert it into VLAN traffic that is forwarded to WAN or Internet;
Security access control between hirers is realized;
Malicious code prevention and intrusion prevention are carried out for different hirers and borders. The defense is based on WEB application attacks;
Identify, monitor and defense abnormal traffic and unknown threats.
Resource and security management center
To meet the requirement of the classified security protection system construction in the coming cloud computing age 2.0, ABT provides security visualization platform solution; on the basis of the cloud computing security defense system, the security visualization platform is built to realize security capability at the three layers, including the basic policy layer, traffic analysis layer and capability superimposed layer:
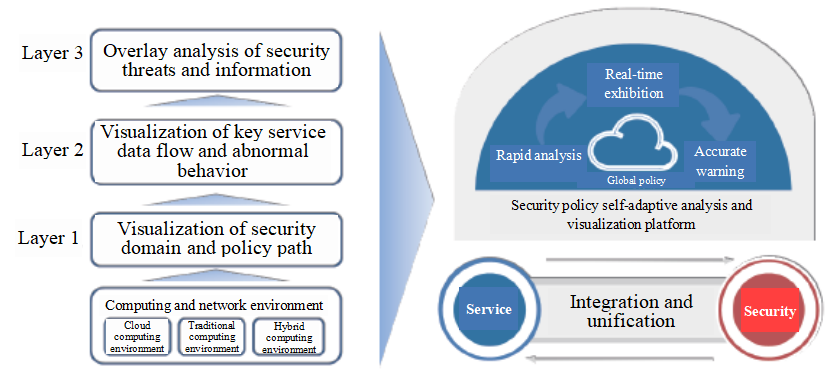
Specific implementations of security visualization platform in the cloud computing environment are as follows:
Virtual network architecture visualization in the cloud computing environment
Automatic extraction and analysis of security policy information of equipment like virtual firewalls, virtual routers and virtual switches are realized, including routing information, access control policies, NAT policies. Visualization technology is used to carry out visualization demonstration of internal network security infrastructure of cloud computing.
Cloud security policy management visualization
Manage and change visualization of security policy of security policies of corresponding nodes in the cloud computing, analyze redundancy, conflicts and invalid strategies of related equipment as well as help users get rid of user configuration risks. Based on workflow and user permission, the whole flow of policy change application, analysis and examination is visualized.
Traffic security visualization
DPI in-depth identification and big data technology identifies multi-dimensional service types, e.g. user, network, application, protocol and server, monitoring network indicators such as specified service traffic, dialogue, delay, success rate, length of packets and access region, counting service indicator baseline, warning indicators that surpass the baseline and carrying out historical information retrospective analysis.
Cloud security capability superimposition and threat visualization
The capability of rapid retrieval and mining of massive data at any period and effective superimposition of different security inspection and defense makes it possible to carry out data association based on the big data technology, screening, filtering, mining, analyzing and realizing visualization of integrated network security situation including security path, service traffic security issue and threat information.
Industry cloud security solution value
Virtualization scheduling and policy visualization management of security capability
Defense and inspection of Web application layer and API interface
Virtualization security defense and inspection
In-depth user behavior analysis and threat precaution
Panoramic network traffic, monitoring and analysis
Cloud-based unified identity authentication and cloud resource management
Asset protection and audit of core data

