Hospital classified security protection visualization solution
Background briefing
With medical and health system reform going into further depth, hospital information system has become a very important part in medical service mechanism. As medical information leakage issues happen repeatedly, classified information security protection has been listed as the important examination basis and indicator of informatization standard construction in Evaluation Standard of General Hospitals of Three Grades since 2011. In December of the same year, the Ministry of Health issued the Notification on the Management of General Office of the Ministry of Health of Overall Classified information security protection in the Health Industry, demanding the health industry to launch “overall classified information security protection”.
Demand analysis
As the crucial guarantee of hospital system operation and cooperation among departments, the stable operation of hospital information system is confronted with the following challenges in information security construction:
Policy compliance
Hospital information security construction shall be in accordance with classified information security protection rules
Suit actual application environment of the hospital
Security construction can meet the demands of the stable, efficient and extensible hospital services
Easy to use
Security construction shall neither enhance the existing network management difficulty nor increase much workload to equipment or policy maintenance
Construction content and effect visualization
All network security issues can be demonstrated, monitored and managed in the classified protection construction; security protection effect statistics can be shown with digital report forms. Security of the network can be known clearly
Solutions
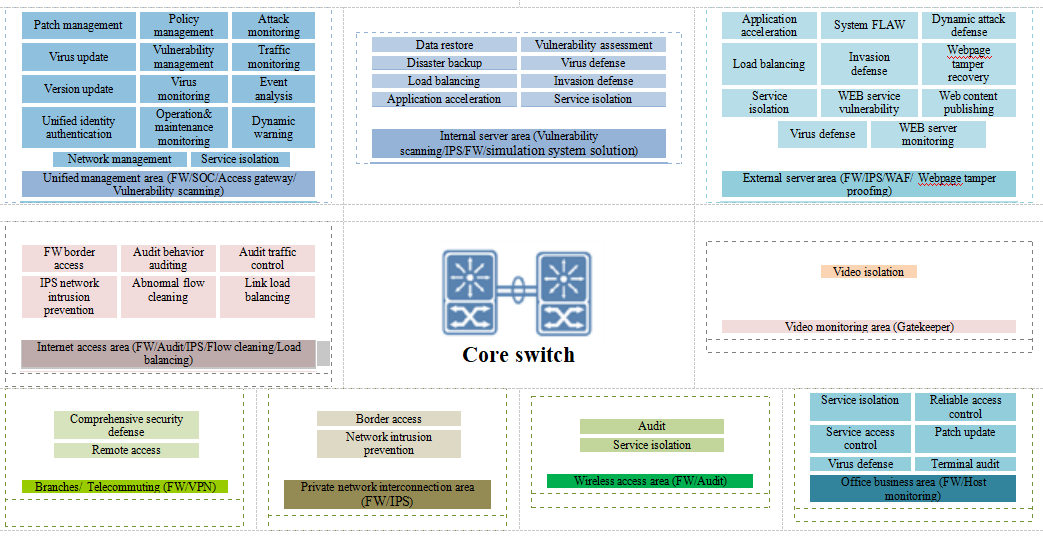
Taking into account related requirements for classified protection, hospital information security construction provides overall protection strategies from the three aspects of prevention in advance, control in action and traceability to enhance hospital security capability in an all-round way.
The protection shall focus on external Web applications to reduce data leakage risks. At the same time, malicious accesses and attacks shall be controlled and blocked;
VPN technology is adopted to ensure the security and reliability of the data transmission between the hospital and other institutions;
Strengthen proactive defense capability and enhance usability of information system through security risk analysis that is all-dimensional and multi-perspective;
Centralized and visualized management means is used to avoid idle equipment or unusable equipment;
Implement and improve classified protection construction according to related requirements higher authorities and the classified protection system.
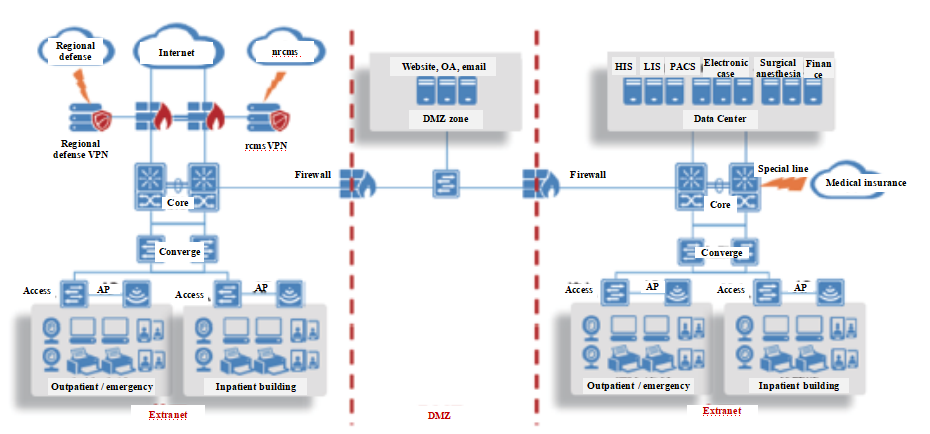
Topological graph:
The traditional solution of physical isolation of Intranet and Extranet:
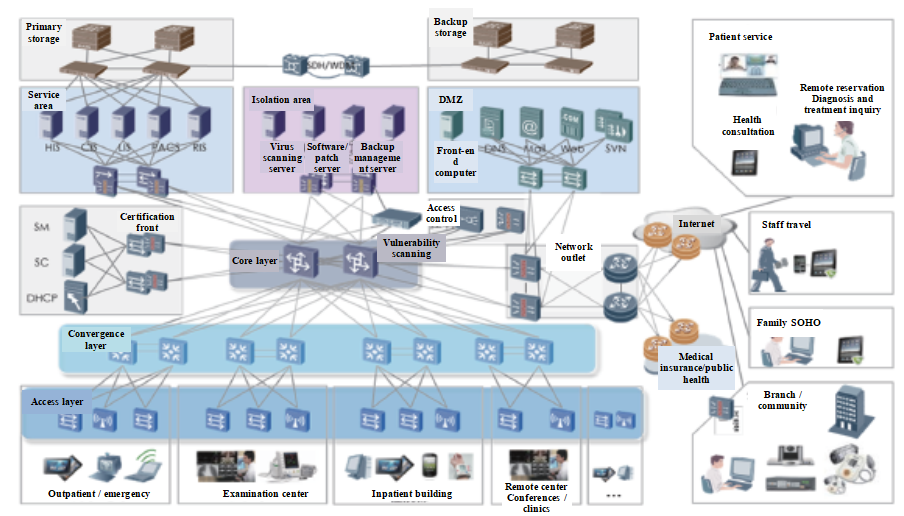
ABT security visualization solution in the classified protection age 2.0
In order to meet the demands of classified security protection system construction of the medical industry related information system in the new age, ABT provides security visualization solutions with the following value for users:
Network security path overall visualization of critical service system
Correlated visualization of service quality, user behavior, abnormal traffic and security risks
Enhance security forecast and defense capability by visualized awareness of network security risks
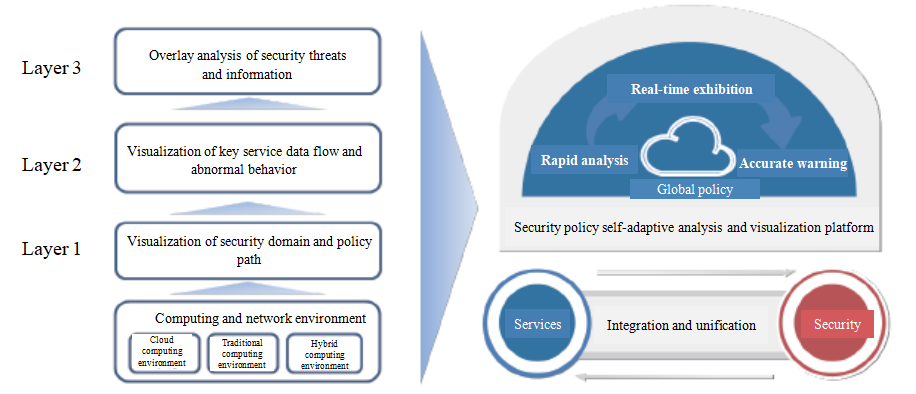
On the basis of the basic network structure and traditional security defense system, the security visualization layer is built to realize security capability at the three layers, including the basic policy layer, traffic analysis layer and capability superimposed layer. Specific implementations are as follows:
| Visualization of security domain infrastructure Automatic extraction and analysis management of equipment like network firewalls, routers and switches shall be implemented. Routing information, access control and NAT policy that affect data security are included. Visualization technology is used to realize visualization of enterprise network security domain infrastructure. | | Visualization of security compliance path On the basis of the status quo of customer industry and the enterprise’s business flow, application structure and data structure, compliance baseline policy of core service systems’ critical data to realize layer query of the security domain infrastructure, demonstrate compliance path based on service, forecast network risks and carry out visualization analysis of the core service threat level. |
| Visualization of security baseline matrix By analyzing enterprise intranet security policy system and service system, security policy matrix between security domains, systems and users and the systems are established to visualize security policy compliance matrix. Violation of policy baseline behavior is automatically warned visually through sustained monitoring on baseline. | | Visualization of security policy management Manage and change visualization of whole network security policy, analyze redundancy, conflicts and invalid strategies of related equipment as well as help users get rid of user configuration risks. Based on workflow and user permission, the whole flow of policy change application, analysis and examination is visualized. |
| Visualization of traffic security DPI in-depth identification and big data technology identifies multi-dimensional service types, e.g. user, network, application, protocol and server, monitoring network indicators such as specified service traffic, dialogue, delay, success rate, length of packets and access region, counting service indicator baseline, warning indicators that surpass the baseline and carrying out historical information retrospective analysis. | | Visualization of security capability superimposition and threats The capability of rapid retrieval and mining of massive data at any period and effective superimposition of different security inspection and defense makes it possible to carry out data association based on the big data technology, screening, filtering, mining, analyzing and realizing visualization of integrated network security situation including security path, service traffic security issue and threat information. |
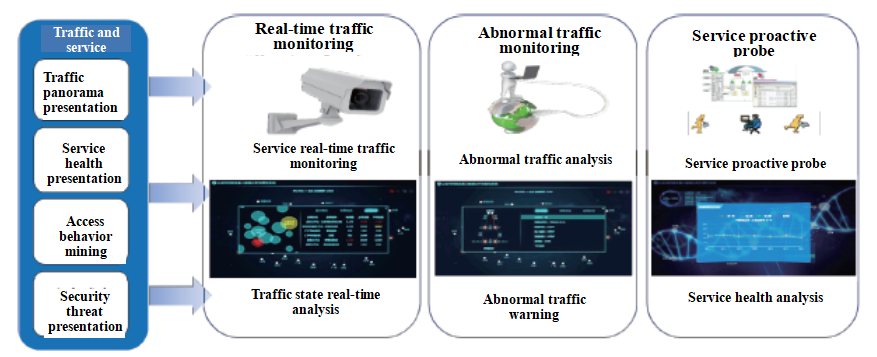
Solution value
Meet the requirements of relevant policies and enhance compliance capability.
Improve security operation maintenance efficiency and save personnel cost of hospitals.
Visualization platform ensures checkable investment and reasonable security construction.
Real-time warning and periodical report information help hospitals find vulnerability that will be inspected and supplied timely.
The guaranteed reliability of hospital information system helps increase patients’ satisfaction.
The guaranteed information sharing promotes continuous increase in regional medical capability.