Visual Security Solution for General Education Metropolitan Area Network
Construction background
Since the beginning of the new century, information technology has permeated all aspects of economic development and social life, making education for all people, quality education, personalized learning and lifelong learning important characteristics of education development in the information age. In front of the increasingly intensified national strength competition, the Outline of the National Program for Medium and Long-Term Educational Reform and Development (2010-2020) (hereinafter referred to as the Outline of Educational Program) points out explicitly, “Information technology has revolutionary influence on education development and shall be paid highly attention.”
Based on the above information, the State Council, the Ministry of Education and Provincial Departments of Public Education issued the following directive policy documents consecutively to promote and guide regional development of educational informatization:
The State Council confirmed the crucial strategic importance of educational informatization in the issued National Program for Medium and Long-Term Educational Reform and Development (2010-2020) and put forward policy requirements and construction target of educational informatization.
The Ministry of Education confirmed the thinking thread, direction and construction target of educational informatization in the issued Ten Year Development Plan of Informatization of the Ministry of Education.
The Ministry of Education issued the Notification on the Establishment of Inter-Department Coordination Group for Promotion of Educational Informatization to coordinate the eight ministries to push forward educational informatization together.
Du Zhanyuan from the Ministry of Education put forward the concept of “three tasks and two platforms”, which were the core target of educational informatization during the “12th five-year plan period”.
Vice Premier Liu Yandong confirmed on the National Teleconference on Educational Informatization that during the “12th five-year plan period”, “three tasks and two platforms” were the core target and sign project of the current educational informatization.
Demand analysis
At present, most regions have begun or completed the construction of education metropolitan area network. Among those regions, many have implemented further construction of wireless network for the gradual promotion of service like distance learning.
However, there are still issues in the construction of general education metropolitan area network, including:
The fact that House of Audio-Visual Education Programme is not able to manage export safety equipment of access units has caused the border security policy management deficiency of the whole network that makes a highly potential security problem and is inconvenient for terminals to change when the policy is adjusted;
Access control policy for various user roles is not visible, so chaos and loopholes are apt to be seen in management;
The hard-to-monitor application quality causes bad service usage experience or conditions in which service cannot be used.
End user authentication is so troublesome that PC, PAD and mobile ends each has their own authentication method and account that causes inconvenience.
Solutions
Given the potential problems hiding in current general education metropolitan area network, ABT puts forward the solution. The following is topological graph of the solution:
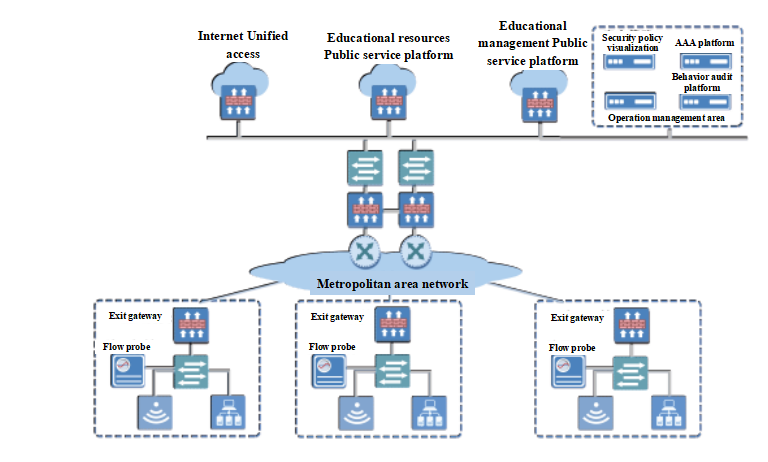
Exit gateway and flow probe products are deployed at exits of access institutions, security policy visualization platform and behavior audit platform at data center.
With the deployment at exit gateways and the cooperation of management platform of data center, we can realize:

The policy center manages security equipment of all access terminals directly, collecting their logs for House of Audio-Visual Education Programme to carry out unified management and supervision. Headquarters and access areas can find warnings. At the same time, the center directly management and issue policy adjustment to access terminals, updating feature library instead of debugging one by one.
The ABT solution that is able to realize terminal integrated authentication greatly has relived end users’ difficulty in utilization greatly.
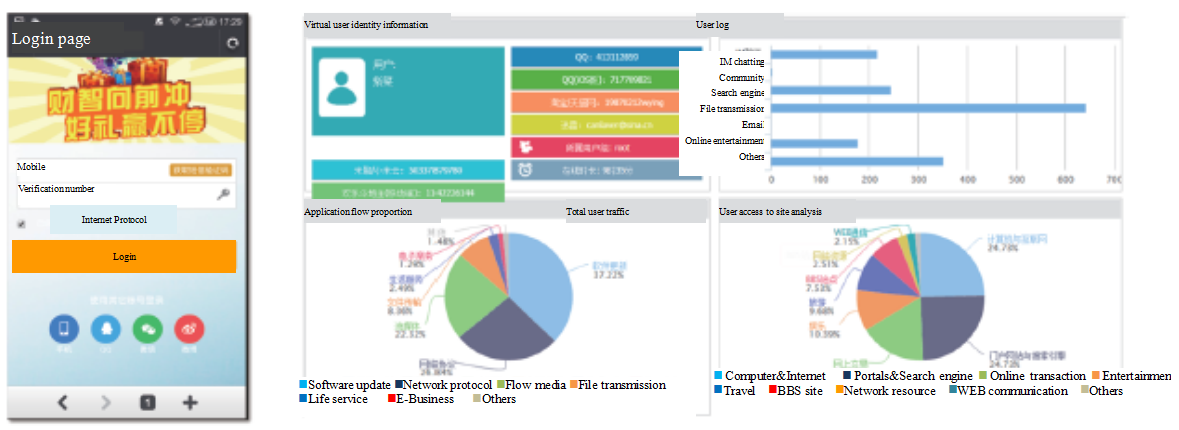
In the light that authenticated users are different, they are grouped before the adjustment of access control policy so as to realize safe and controllable network permission.
As a high-performance network traffic data collection and intelligence analysis hardware platform based on big data and visualization technology, the ABT traffic security visualization platform that is deployed at key nodes of enterprises networks can display overall network operating state, network quality, service quality of application, user access behavior and security threats with rich graphics by conducting multi-dimensional and in-depth data packet content analysis and correlated analysis of mirror traffic to visualize traffic, know behavior and control threats of enterprise networks,
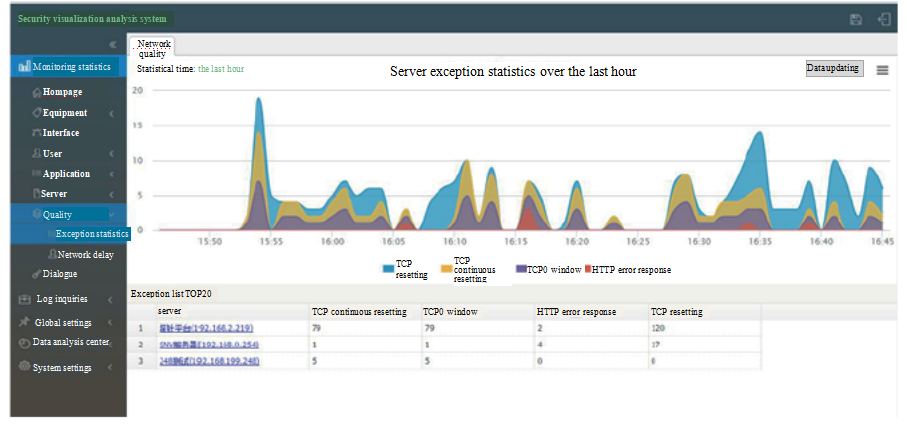
By real-time monitoring traffic of services of the education metropolitan area network, we are able to not only judge health condition of services effectively, but provide effective data basis for later information technology construction as well.
Solution value
Terminal behavior controllability
By grouping user roles, different policies are applied to user groups to ensure security and controllability of the general education metropolitan area network through user behavior audit and analysis.
Security policy visualization
Security policy visualization, service traffic visualization of the whole network and real-time monitoring of services and security equipment ensure security and serviceability of the network and services.
Deployment adjustment convenience
By managing terminal access security equipment uniformly, policy alteration, log collection and exception warning can be processed directly in the center and the network security performance is improved.

